Health problem related with use of ICT
The main risks associated with using computers include:
- Musculoskeletal problems
- Vision related problems
Rashes and other skin complaints have also been reported, although it is thought these are caused by the dry atmosphere and static electricity associated with display units rather then by the display units themselves. There are potential risks from radiation though this is a contentious area.

Musculoskeletal problems
These can range from general aches and pains to more serious problems and include:
- Upper limb disorders such as Repetitive Strain Injury (RSI) tenosynovitis and carpal tunnel syndrome - by far the most important as it can quickly lead to permanent incapacity
- Back and neck pain and discomfort
- Tension stress headaches and related ailments
The basis for this illness concept is the idea that one can overuse a tool, such as a computer keyboard or musical instrument in a way that causes tissue damage leading to pain.
The following complaints are typical in patients that might receive a diagnosis of RSI:
- Pain in the arm (typically diffuse--i.e. spread over many areas).
- The pain is worse with activity.
- Weakness, lack of endurance.
These types of problem can be caused by:
- Maintaining an unnatural or unhealthy posture while using the computer
- Inadequate lower back support
- Sitting in the same position for an extended period of time
- An ergonomically poor workstation set up
Prevention
Several relatively straightforward precautions can be taken by computer users to avoid problems.
Avoiding Musculoskeletal problems
General precautions to avoid musculoskeletal problems include:
- Taking regular breaks from working at your computer - a few minutes at least once an hour
- Alternating work tasks
- Regular stretching to relax your body
- Using equipment such as footrests, wrist rests and document holders if you need to
- Keeping your mouse and keyboard at the same level
- Avoiding gripping your mouse too tightly - hold the mouse lightly and click gently
- Familiarise yourself with keyboard shortcuts for applications you regularly use (to avoid overusing the mouse)
It is also important to have your workstation set up correctly. Your workstation includes monitor, keyboard, mouse, seating, desk, and where appropriate, footrest (to enable you to put your feet flat if they would otherwise not reach the floor), wrist rest, and document holder. Monitors should:
- Swivel, tilt and elevate - if not use an adjustable stand, books or blocks adjust the height
- Be positioned so the top line of the monitor is no higher than your eyes or no lower than 20° below the horizon of your eyes or field of vision
- Be at the same level and beside the document holder if you use one
- Be between 18 to 24 inches away from your face
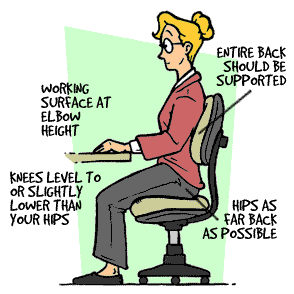
Keyboards should:
- Be detachable and adjustable (with legs to adjust angle)
- Allow your forearms to be parallel to the floor without raising your elbows
- Allow your wrists to be in line with your forearms so your wrists does not need to be flexed up or down
- Include enough space to rest your wrists or should include a padded detachable wrist rest (or you can use a separate gel wrist rest which should be at least 50 mm deep)
- Be placed directly in front of the monitor and at the same height as the mouse, track ball or touch pad
Chairs should:
- Support the back - and have a vertically adjustable independent back rest that returns to its original position and has tilt adjustment to support the lower back
- Allow chair height to be adjusted from a sitting position
- Be adjusted so the back crease of the knee is slightly higher than the pan of the chair (use a suitable footrest where necessary)
- Be supported by a five prong caster base
- Have removable and adjustable armrests
- Have a contoured seat with breathable fabric and rounded edges to distribute the weight and should be adjustable to allow the seat pan to tilt forward or back
Tables and desks should:
- Provide sufficient leg room and preferably be height adjustable
- Have enough room to support the computer equipment and space for documents
- Be at least 900 mm deep
- Have rounded corners and edges
Vision related problems
Computer users can experience a number of symptoms related to vision including:
- Visual fatigue
- Blurred or double vision
- Burning and watering eyes
- Headaches and frequent changes in prescription glasses
Computer work hasn't been proven to cause permanent eye damage, but the temporary discomfort that may occur can reduce productivity, cause lost work time and reduce job satisfaction. Eye problems are usually the result of visual fatigue or glare from bright windows or strong light sources, light reflecting off the display screen or poor display screen contrast.
Avoiding vision related problemsPrecautions include:
- Exercising the eyes by periodically focusing on objects at varying distances
- Blinking regularly
- Keeping the air around you moist - for example using plants, open pans of water or a humidifier (spider plants are said to be particularly good for this and removing chemical vapours from the air)
- Adjusting the screen height / seating so that when sitting comfortably your eyes are in line with the top of the monitor screen
- Adjusting the brightness control on your monitor for comfort
- Adjusting the contrast on your monitor to make the characters distinct from the background
- Adjusting the refresh rate of your monitor to stop it flickering
- Positioning monitors to avoid glare (e.g. not directly in front of windows)
- Keeping your monitor the screen clean
- Keeping the screen and document holder (if you use one) at the same distance from your eyes
- Servicing, repairing or replacing monitors that flicker or have inadequate clarity
- Regular eye testing - do this at least once every 2 years and more frequently if necessary - especially if you are experiencing eye problems related to using display equipment. Indicate the distance from your eyes to the monitor to your optician and talk to them regarding special lenses or the use of bifocals.
There are a number of security/safety issues related with the use of computers. Some of them are
- Hacking
- Virus
- Logic Bomb
- Pishing
- Software piracy
Hacking
Hacking is defined as unauthorised access to data held in a computer system. A hacker is someone who uses their knowledge of computers to break into other computer system. Once a hacker gets access to a computer system, he might steal important information or might delete important files to produce disruptions in the smooth working. As per the Computer Misuse Act, hacking is illegal.
Individual computers or networks can be protected from hacking by using ‘firewall software’.
Virus
Viruses are generally developed with a definite intention to cause damage to computer files or at the very least cause inconvenience and annoyance to computer users. A virus usually attaches itself to a program or file and t hen copies itself into other programs and files with which it comes in contact.

Types of Virus
Trojan horses
The 'Trojan Horse' is a very apt name for a particularly nasty type of virus. Although technically not a virus, a Trojan Horse is in many ways a more important treat to be aware off. A Trojan Horse must be installed on your computer to become effective. The Trojan Horse has the ability to attach itself to another programme then install itself onto your machine covertly when you install the programme it resides within.
Many Trojan Horses are 'key-logger' programmes that record every key press on your keyboard and store them in a log file. This log file is then e-mail to the person who sent the Trojan Horse to you in a convert way every time you access the Internet. Everything you type; e-mails, letters, credit card numbers, passwords, phone numbers etc. are all logged and received by the hacker, your privacy is completely compromised. Some more advanced key-loggers or password sniffers also keep account of all of the web sites that you have visited and when.
Worms
Worms have the ability to replicate themselves, and generally do not require human interactivity to do so. They may be designed to e-mail themselves to other computers. Worms copy themselves from computer to computer rather than file to file like most viruses, and because they require no human help to do so, they can spread much more rapidly through a system than a normal virus.

A Worm may arrive in an unsolicited e-mail in an attachment that tempts you to open it, once you do the worm spreads to your computer. E-mail Worms that have the ability to replicate and e-mail themselves to many people simultaneously have resulted in the crashing of e-mail severs in the past due to the excessive strain of all the traffic!
Protection against viruses
When it comes to protecting your computer from virus the proverb ‘Precaution is better than cure’ is very much applicable. Some precautions could be
- Any executable .EXE files should not be opened unless you trust the sources.
- Never open unsolicited e-mail.
- Use reliable virus protection software.
- Always use computer firewall. Firewall software acts as a secure barrier between your computer and the outside world. It monitors all traffic to and from your computer, and decides whether or not this is normal Internet activity or an unauthorised security risk.
- Avoid using flash discs, floppy disc which were used on other computer. In case you cannot avoid, do a virus scan before using these devices.
- Viruses may spread through infected floppy discs, flash drives (pen drives), downloads from internet or through e-mails.
Logic bombs
Logic bomb is a set of instructions written in computer code that can be hidden inside other software and set to activate at a particular data and time. A logic bomb could also be programmed to wait for a certain message from the programmer. The logic bomb could, for example, check a web site once a week for a certain message. When the logic bomb sees that message, or when the logic bomb stops seeing that message, it activates and executes it's code.
Phishing
Phishing (password harvesting) is an illegal activity where someone attempts to acquire sensitive information such as user names, passwords and credit card information. Often, users are asked to enter these details onto a website which they are stolen from.

Pishing
The term Phishing originates from the internet argot leetspeak. Phishing often employs highly advanced imitation websites which steal digital information, however they often employ simpler messages like emails requesting bank information disguised as a desperate cry for financial help or a random donation from a wealthy individual.
The purpose of the fraudulent sender is to "phish" for, or entice people to share, their personal, financial, or password data. It's then used to commit crimes.
Software piracy
Software piracy is the illegal distribution and/or reproduction of software applications for business or personal use. Whether software piracy is deliberate or not, it is still illegal and punishable by law.

software piracy is a real threat to the software industry
Kinds of piracy
End User Piracy
Using multiple copies of a single software package on several different systems or distributing registered or licensed copies of software to others.
Another common form of end user piracy is when a cracked version of the software is used. Hacking into the software and disabling the copy protection or illegally generating key codes that unlocks the trial version making the software a registered version creates a cracked version.
Reseller Piracy
Reseller piracy occurs when an unscrupulous reseller distributes multiple copies of a single software package to different customers this includes preloading systems with software without providing original manuals & diskettes. Reseller piracy also occurs when resellers knowingly sell counterfeit versions of software to unsuspecting customers.
Trademark/Trade Name Infringement
Infringement occurs when an individual or dealer claims to be authorized either as a technician, support provider or reseller, or is improperly using a trademark or trade name.
Internet Piracy
Internet Piracy occurs when there is an electronic transfer of copyrighted software. If system operators and/or users upload or download copyrighted software and materials onto or from bulletin boards or the Internet for others to copy and use without the proper license. Often hackers will distribute or sell the hacked software or cracked keys. The developer does not receive any money for the software the hacker distributed. This is an infringement on the developer's copyright.
Widspread use of ICT has affected the way people work and has reshaped our present workplaces. Some of the effects are:
Unemployment
- The introduction of computers made many jobs outdated.
- For example typists were replaced by people who could use a computer to word process documents. These documents could be saved to disc and recalled whenever needed instead of being re-types.
- Some routine (boring) jobs were replaced by automatic machines controlled by computers. Or we find that a person employed to record variables on a production line is no longer needed as either the operators enter these via a keyboard OR a remote data logging system records them.
- Some very dangerous jobs where conditions were unpleasant were replaced by robot-type machines making the work much safer. The system parameters of a chemical plant are far easier to control using a computer than human operator. Heavy Chemicals has seen an 80% reduction in workforce over the last 20 years.
New jobs created
- New skills are needed to use the computer software and hardware. More operators are needed to process the increase in trunover generated by quick and easy access to applications.
- Programmers to write the instructions to make the computers work.
- Engineers to build the automatic machines.
- Systems analysts to design business software systems etc.
- People working at a drawing board may no longer be needed - but people who can use CAD programs are in huge demand - one local firm had to recruit from other parts of Europe because there were very few people in Britain with the high-tech skills they were looking for.

ICT has lead to a rise in demand for IT professionals
Working hours
- Some people may work less hours as a result of automation and the introduction of IT into the workplace.
Retraining
- The switch to computerised systems involves considerable retraining and means that a modern society needs to have a more flexible workforce. The rapid advances mean individuals may have to retrain for employment several times during their working lives.
More leisure time
- As a result of the drop in working hours for some people - however some of this leisure time is not by choice - it is because of unemployment or because they can only find part-time or casual work.
De-skilling of jobs
- Some jobs which were highly regarded in the past have lost their value because computers have take a lot of the skill out of them - for example a checkout operator at a supermarket now has to simply pass each item across a bar-code reader - all the processing of the information is carried out automatically and the change to be given to the customer is calculated. Skilled machinists now find that the computer, once “taught” is able to produce consistently better products.
Information Technology in the Workplace
Much of the attention IT has garnered is due to its unique power and speed, the diversity of IT applications in the workplace, and its recent, pervasive presence. Although many definitions are possible, IT can be defined as capital equipment that makes extensive use of microelectronics and programmed instructions or software. IT systems are often flexible, reprogrammable, and automatic or self-acting. They can record, process, communicate, and react to vast amounts of information entered by users, received from the environment, or stored internally.
Prominent examples of IT specific to manufacturing and similar blue collar jobs include numerically controlled and computer numerically controlled machine tools,
- robots,
- computerized diagnostic and testing equipment,
- manufacturing process controls such as programmable logic controllers,
- automated material handling equipment, automated guided vehicles,
- factory local area networks (LANs),
- computer-aided design and manufacturing (CAD/CAM),
- material resource planning software to manage supplies and inventory,
- flexible manufacturing systems that integrate many of these technologies into more fully automated systems.

Prominent information technology applications in office and service sector environments include
- common desktop applications such as word processors, spreadsheets, databases, e-mail clients,
- and Internet browsers;
- data entry and transactions processing systems (e.g., payroll, billing, bank transactions, and insurance claims);
- LANs;
- CAD;
- automatic teller machines;
- bank networks for electronic funds transfer;
- electronic data interchange for automated ordering and payment between purchasers and suppliers;
- barcode scanners; and
- point-of-sale devices.


Survey data indicate that the share of workers using computers with video screens and keyboard input on the job has increased tremendously. Popular applications include word processors, database and spreadsheet programs, and, more recently, e-mail clients and Internet browsers. Much less systematic data exist on most of the other applications noted above.




